TechTalk Daily

Threats posed by nation-state hackers and intrusive apps are a result of “tech-based hybrid warfare” being waged by China, Russia, North Korea, Iran and other bad actors worldwide who are exploiting vulnerabilities within operating systems and popular apps that are distributed by Google, Apple, & Microsoft.
Furthermore, Google, Apple and Microsoft are enabling app developers from China and Russia to monitor, track, and data mine the Android OS, Apple iOS and Microsoft OS end user for financial gain as a result of partnerships with Chinese and Russian corporations that include:
Consistent with unrestricted hybrid warfare, “tech-based” hybrid warfare targets everyone, including:
This means that nation-state hackers, plus Chinese and Russian companies, are weaponizing endpoint devices supported by these popular operating systems as a means to launch attacks on any network, including critical infrastructure.
Additionally, app developers from adversarial countries are using popular apps and social media platforms, such as TikTok and WeChat, as vehicles to surveil and data mine the Android OS, Apple iOS, and Microsoft Windows OS end user for profits 24x7/365 days per year, whether the end user is an adult, teen, child or business/government end user.
ByteDance’s social media app TikTok, which can be described as “legal malware”, is being distributed by way of app stores owned by Microsoft, Google and Apple, as well as preinstalled software that is included with the Microsoft Windows 11 OS, posing massive privacy and cybersecurity threats to billions of Microsoft Windows 11 OS end users, including business end users, worldwide.
For example, a single intrusive app enables the developer, including those from China and Russia, to conduct surveillance on the end user while enabling the developer to collect more than 5,000 highly confidential data points associated with the end user’s personal, business, medical, legal and employment information as a result of the app user using their smartphone for personal, business and employment purposes.
What is more concerning about TikTok is the fact that a member of the Chinese government was added to the board of directors for ByteDance exposing corporate information to the Chinese Government according to a 2021 Bloomberg/Yahoo Finance Report.
This means that TikTok end users could be exposing highly confidential personal and business information to the Chinese Communist Party (CCP) posing massive cybersecurity and privacy threats to TikTok end users, including the end user’s employer.
Today endpoint cybersecurity is not being addressed 100% by chief information officers (CIOs), chief information security officers (CISOs) or IT/cybersecurity professionals due to a hyper focus on traditional network cybersecurity.
As a result of “tech-based hybrid warfare”, nation-state hackers from China, Russia, North Korea and Iran are exposing vulnerabilities within the Android OS, Apple iOS and Microsoft Windows OS to launch ransomware, distributed denial of service (DDoS) and man-in-the-middle (MITM) attacks on networks, including critical infrastructure.
Aside from the OS, intrusive apps that support smartphones, tablet PCs, connected products and PCs are also being used to launch attacks on networks while enabling the developers to monitor, track, and data mine the end user posing massive privacy and cybersecurity threats to the end user, plus the end user’s employer.
For example, Lazarus, a North Korean state-sponsored hacker group, recently exploited Microsoft’s Windows OS to launch Trojan horse malware attacks on networks rather than using traditional hacking methods centered on infiltrating a network via telecom infrastructure or using email phishing to launch an attack according to a report by ESET security researcher Anton Cherepanov.*
*source Hacker News Nov 15th, 2021
As I reported in my 2019 MissionCritical Communications Magazine article, “The Rise of Foreign Cybersecurity Threats”, vulnerabilities within the Microsoft Windows 10 OS were used by Russian state-sponsored hackers to launch attacks by way of Triton Trisis malware targeting industrial control systems (ICS) of the Petro Rabigh oil refinery in Saudi Arabia in order to cause an explosion.
Triton Trisis evolved from NotPetya ransomware, also known as (Black Energy Malware, which is used by Russian state-sponsored hackers to attack critical infrastructure within Ukrainian utilities as part of Russia’s invasion of Ukraine.
NotPetya, plus other ransomware, is known as “crash-override malware” which can be installed by using plug-ins associated with the Windows OS and Linux, posing massive cybersecurity threats to critical infrastructure, including internet of things (IoT)/industrial IoT (IIoT) devices, and industrial control systems (ICS).
“An attacker could use the serial number with the DEP (device enrollment program) API (application programmable interface) to retrieve the activation record (or DEP profile) and leak information about the organization, or be used in social-engineering attacks to, for example, call the help desk and give them the serial number asking for help ‘re-enrolling’ in the MDM server,” Barclay explained during an interview conducted by Lindsey O’Donnell of Threat Post in 2018.
As of this date, there is no record of Apple fixing this issue.
Unknown to most Apple product owners and users is the fact that Apple uses servers located in China to store iCloud information uploaded by Apple iOS end users according to a CNN report.
Apple using critical infrastructure in China associated with iCloud is another example of why the U.S. government needs to mandate that technology providers and manufacturers decouple critical infrastructure, including manufacturing, from China, especially since China continues to be a threat to Taiwan while using forced labor associated with manufacturing.
As I have reported in the past, nation-state hackers from around the world have infiltrated popular app stores to have their intrusive malware inadvertently distributed by tech giants such as Google who have removed hundreds of these dangerous apps from Google Play over the past few years, however the problem still persists today.
As reported by Tech Radar, June 13th, 2022, over a billion android apps that have been downloaded from Google Play could be infected with malicious malware, some of which could have been developed by nation-state military grade hackers from China or Russia.
The use of Triton Trisis, and other malware that can be launched by way of operating systems, intrusive apps and MDM security platforms pose massive threats to utilities, governments, energy companies, the military and other entities supported by critical infrastructure.
Although, Mobile Device Management (MDM) platforms will help secure connected devices, such as smartphones, by blocking intrusive 3rd-party apps that are downloaded by the device user, MDM device platforms will not protect the end user from intrusive apps that are preinstalled into smartphones, tablet PCs, IoT/IIoT devices, connected products and PCs supported by the Android OS, Apple iOS or Microsoft Windows OS.
For example, Chinese surveillance and data mining technology** was preinstalled into millions of Samsung Smartphones supported by the android OS as a result of a partnership between Google and BAIDU, see enclosed screen shot for reference:
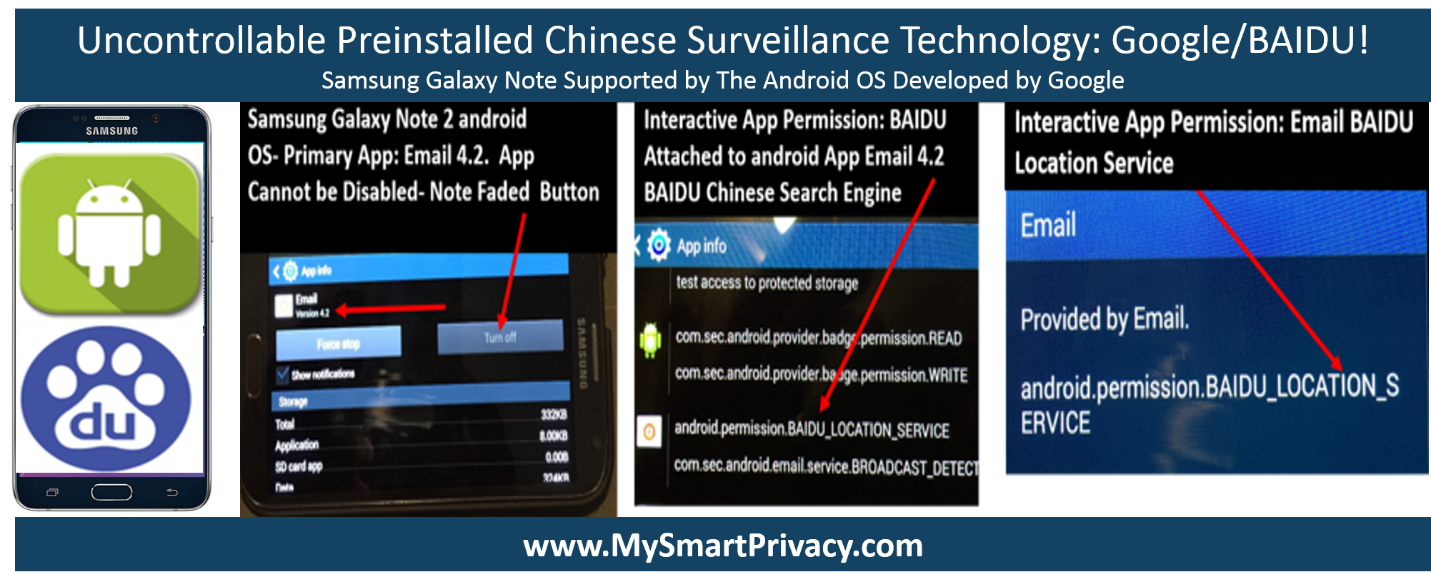
According to T-Mobile and Verizon***, any connected device supported by the Android OS, Apple iOS, or Microsoft Windows 8, 10, or 11 OS cannot be fully privatized or secured due to uncontrollable preinstalled surveillance & data mining technology in the form of intrusive apps developed by Google, Apple and Microsoft, plus their developer partners, including those from China such as ByteDance and BAIDU.
***T-Mobile Admission (FCC consumer complaint #423849, July, 2015)/Verizon request July, 2018
The reason the Android OS, Apple iOS or Microsoft Windows OS cannot be fully privatized or secured is due to the fact that all operating systems concerned are developed using an open application programmable interface (API) architecture in order to support intrusive apps which enable app developers to conduct surveillance on end users while data mining highly confidential personal and business information from the OS end user to exploit for profits.
Aside from being intrusive, many popular apps and social media platforms are intentionally designed to be addictive, posing safety threats to the end user as admitted by Meta (Facebook) cofounder Sean Parker during an Anxios interview in 2017.
This is what Mr. Parker had to say: “It’s a social validation feedback loop, the kind of thing that a “hacker” like myself would come up with, because you’re exploiting a vulnerability in human psychology … God only knows what it is doing to our children’s brains … It’s me, it’s Mark (Zuckerberg), Kevin Systrom of Instagram, it’s all of these people, understood this consciously…And we did it any ways.”
China and Russia are using the Android OS, Apple iOS, Microsoft Windows OS, intrusive apps, and social media platforms as a means to conduct hybrid warfare, attack networks, conduct corporate espionage, spread propaganda (misinformation/disinformation), disrupt elections, and conduct surveillance and data mining on technology users around the world.
The fact is Google, Apple and Microsoft are dependent on profits as a result of partnering with Chinese and Russian companies beholden to their governments, including the Chinese Communist Party (CCP), so these U.S. tech giants are not going stop distributing intrusive Chinese and Russian apps and social media platforms any time soon.
For example, even in light of Russia’s invasion of the Ukraine, Google still distributes intrusive apps developed by Russian companies such as Prisma Labs whose headquarters are in Moscow.
Additionally, Chinese and Russian companies are enabled by the U.S. government to hire powerful K-street law firms/lobbyists in order to influence U.S. lawmakers such as the case with ByteDance (TikTok-China) who hired American Continental Group (ACG) and lobbyist David Urban who was a former advisory to former President Trump.
Today, there are many former executives from Google and Facebook that are now members of the Biden administration, such as former Alphabet/Google Chairman & CEO, Erich Schmidt as reported by Political.
Due to massive profits as a result of predatory surveillance and data mining business practices rooted in “Surveillance Capitalism”, companies and government entities need to adopt best practices associated with endpoint cybersecurity in order to protect their networks, as well as their confidential and protected information including, intellectual property (IP) and classified information.
It is up to companies, academic institutions, healthcare providers and government agencies (local, state & federal) to implement best practices and administrative controls when it comes to the use of connected technology such as:
For more information on how to protect your connected products and technology, visit My Smart Privacy at: www.MySmartPrivacy.com
– Rex M. Lee
Rex M. Lee is a Privacy and Cybersecurity Advisor, Tech Journalist and a Senior Tech/Telecom Industry Analyst for BlackOps Partners, Washington, DC. Find more information at My Smart Privacy, www.MySmartPrivacy.com and see Rex speak at IWCE 2022 in Las Vegas on March 21.